You create a customer bank access for a financial institution. The application supports bank accesses with the protocols EBICS and FinTS.
The function for working with FinTS is not part of the standard scope of the application.
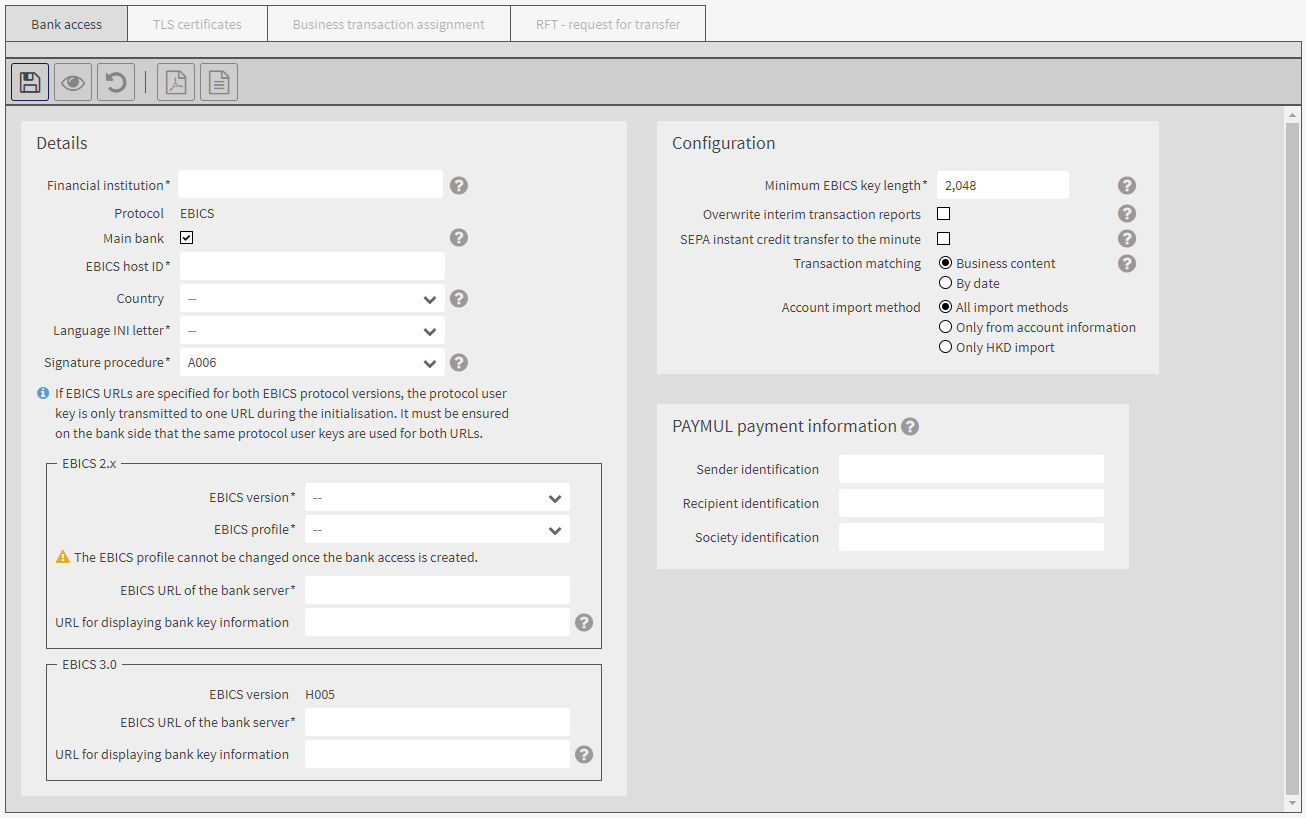
For an EBICS customer bank access you define the URL of the EBICS server, the EBICS version and the EBICS profile. If the separate authorisation for the creation of MT101 orders has been assigned to you, you can assign instruction keys for the creation of MT101 orders.
In order to use the EBICS customer bank access, the user must initialise an own bank access for the customer bank access and activate his bank keys.
For a FinTS bank access you enter the data of the financial institution. Finally, you download the TLS certificate from the server of the financial institution.
Customer bank accesses are permanently assigned to one customer.
You have the data on the bank access for the financial institution.
Your user ID is assigned the rights Customer bank accesses: edit (customer) and Customer bank accesses: read (customer).
Your customer may generally create new EBICS and/or FinTS bank accesses. This setting can be checked in the mask , tab Basic data, field Supported bank accesses.
|
1. |
Select , tab Customer bank accesses. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
2. |
Click on |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
3. |
Only if you can also create FinTS bank accesses: select Create EBICS customer bank access.
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
4. |
Enter the data of the bank access:
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
5. |
If you have entered all data correctly, go to the tab TLS certificates.
The certificate is required for the encrypted transfer of data between the portal and the EBICS server. The users can only use the bank access if the certificate has been accepted (provided that the bank access is assigned to them). On this tab, the known details of the certificate and the issuer are displayed. The value in the field Certificate status has the following meaning:
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
6. |
If the certificate has not been accepted automatically: Click on Download TLS certificate.
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
7. |
Check the authenticity of the certificate. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
8. |
If you are certain that the certificate was issued by a trustworthy certification authority, click on Accept TLS certificate.
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
9. |
On the tab Business transaction assignment you can assign order types (for EBICS 2.x) and/or BTFs (for EBICS 3.0) to business transactions. The assignment serves to uniquely define business transactions for this bank access regardless of the EBICS version used. For a newly created bank access, the assignment is initialised with the existing assignments for EBICS 2.x and EBICS 3.0.
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
10. |
Only with separate authorisation (not part of the standard scope of the application): in the tab Push-Server you configure the connection to the TRAVIC-Push-Server. If you activate this functionality, at their own bank access the users can configure which messages they wish to be notified of for this customer bank access via push message. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
11. |
Only with separate authorisation (not part of the standard scope of the application): in the tab RFT – request for transfer you assign instruction keys to the bank access. Later the user can select the instruction keys during the creation of MT101 orders (order type RFT). |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
The customer bank access has been created.
Based on this customer bank access, bank accesses for protocol users can be created. The procedure is described in the section Creating your own EBICS bank access.
The users of this customer are informed after their next login via a notification on the start page that a new bank access has been created which they can initialise.
The FinTS customer bank access has been created.
Based on this customer bank access, bank accesses for protocol users can be created. The procedure is described in the section Creating your own FinTS bank access.
The users of this customer are informed after their next login via a notification on the start page that a new bank access has been created for which they must specify a PIN if they want to use it.
 .
.